This is a tutorial to teach you guys how to make a program-specific whitelist of IP connections. After this whitelist is made, the program can only communicate with IP addresses that have been mentioned in the Whitelist. Otherwise, the connection will fail. This is an efficient way to control how your programs will respond to unidentified connections. This process is really simple and requires you to make use of the advanced settings in your Windows firewall.
This method outshines others as it only uses the native settings of Windows, unlike some of the third party firewalls which may or may not work. Users can restrict connections based on protocols, specific ports and services too. This feature helps you single out intra-program services that have to be blocked specifically. For example, you might want to stop an application from downloading an update from its developer’s website. But on the flip side, you need to download extensions from the developer’s website too. I however, will use it to employ parental control on one of my browsers.
If Windows Firewall isn’t your thing, make sure you try out this list of firewalls. Most of these have the ability to make firewall rules. This will enable you to mimic this tutorial on the selected firewall.
How to Set Firewall Rules to Whitelist IP Addresses in an Application
My 7 year old niece loves exploring the internet. But we all know that the internet is dark and full of terrors. To keep her safe, I decided to whitelist a handful of websites on a web browser that only she will use. I chose Firefox for the purpose and opened up Windows Firewall settings in the Control Panel. Advanced settings is on the right of the Firewall’s interface. Here is where all the magic happens.
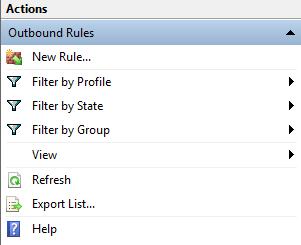
There are two types of rules you can make according to the type of connection. There are inbound connections (server to application) and there are outbound connections (application to server). First we’ll make an outbound rule to prohibit Firefox from connecting to servers other than the whitelist. Clicking New Rule in the outbound rule tab will open the New Outbound Rule Wizard.
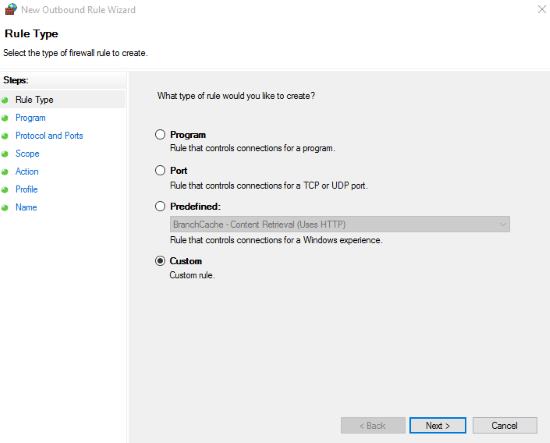
A choice of rule types will appear. Since we need to make a rule with specific criteria, we’ll go with Custom and click Next.
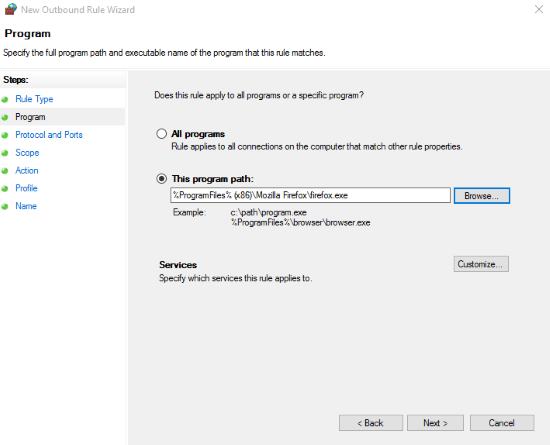
Consequently, you’ll have to choose the application you want to dedicate this rule to. I selected the path to the Firefox executable as mentioned before. Users can make the blocks protocol and port specific under Protocol and Ports. Since we need to apply this rule on all of the ports and protocols, we’ll skip this step.
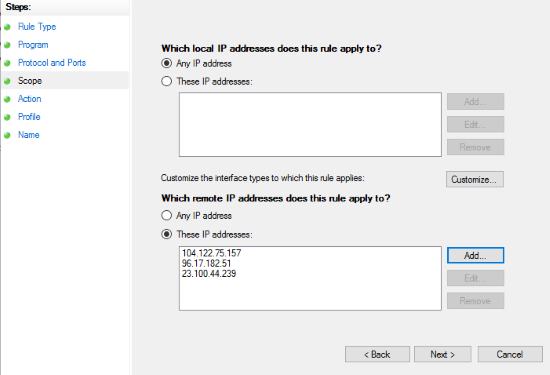
Under scope, you have to enter the IP addresses of websites/servers you want to whitelist. I chose these websites for kids which I’ll restrict my niece to use. To get the IP address of a website, you’ll have to ping it in the command prompt. Local IP addresses only restrict connections in the local network.
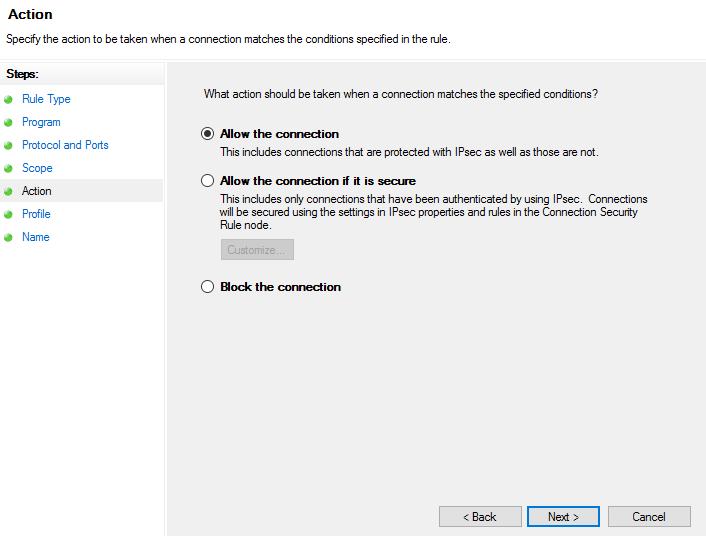
Next, in Actions, Allow the Connections has to be selected to make the base of the whitelist rule. Finish it off by selecting its profile (circles where this rule will be enabled), name and description.
You now have an outbound whitelist for selected websites. Follow the same steps to make an inbound rule. Most important action after setting the rules is to TURN OFF predefined rules already in the firewall that allows the application to connect to any server. If you do not follow the above, this method will not work.
Final Words
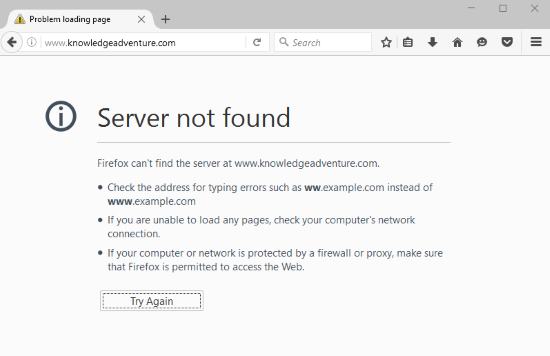
As you can see this method works seamlessly without the use of third party applications or editing the host file in Windows to block all the incoming connections except a few selected ones. If you know a better way to make a software-specific whitelist, share it in the comments!